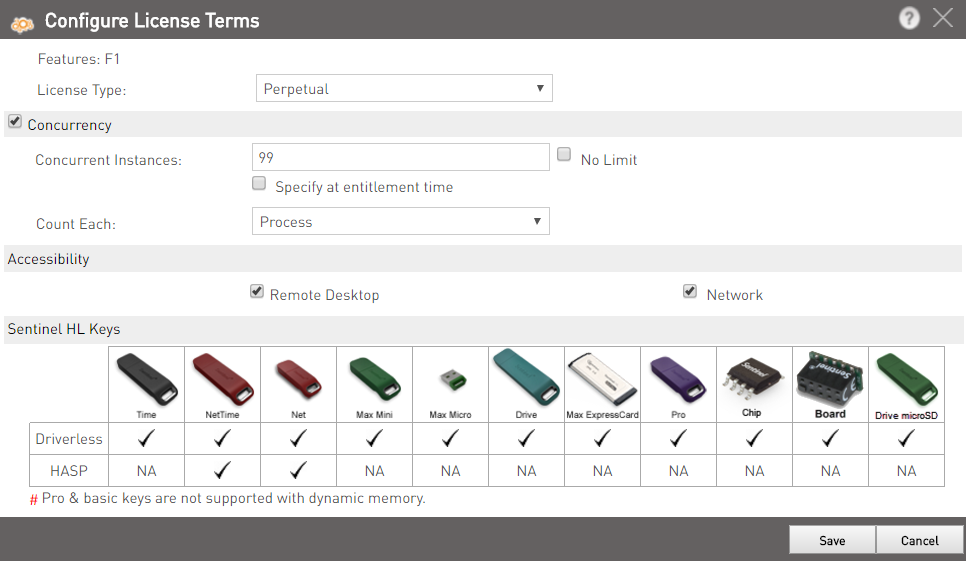
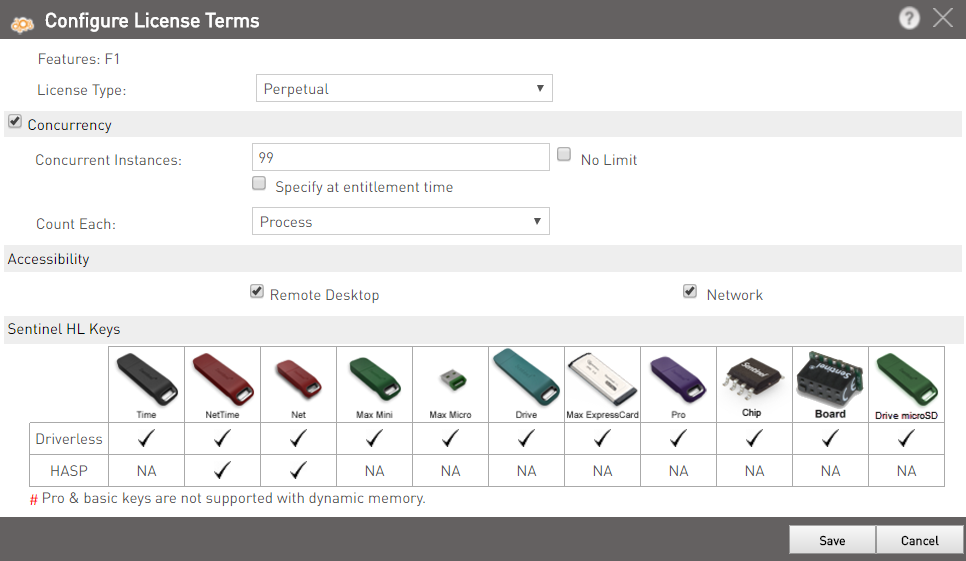
If you need to change the locking type, you must first remove all the Features from the Product Features list. Then, in the Locking Type drop-down list, select the protection level for the Product:
- HL—The Product can be supplied with Sentinel HL keys only.
- SL User mode—The Product can be supplied with stand-alone Sentinel SL keys only.
- SL Admin mode—The Product can be supplied with network Sentinel SL keys only.
- HL or SL Admin mode—The Product can be supplied with either Sentinel HL keys or Sentinel SL keys (network).
- HL or SL (Admin mode or User mode)—The Product can be supplied with either Sentinel HL keys or Sentinel SL keys (network or stand-alone).If you prefer not to specify the protection level in advance, you can assign this locking type to a Product. With this locking type, the decision on which type of Sentinel protection key is to be shipped with the Product is made when each Entitlement is processed.
A Product that has been defined with the Sentinel HL or SL locking type is always supplied with the Sentinel SL key-level of protection, even when it is shipped with Sentinel HL keys.
If Sentinel SL locking type is selected, the Clone Protection drop-down list appears so that you can choose a clone protection scheme. By default, this drop-down list is visible on the user interface(Software that is protected by a Sentinel HL key is not vulnerable to machine cloning).
Only Products that contain features will be clone protected.
Specify the clone detection scheme from the following:
| Platform Default | The platform default clone protection schemes are decided on the basis of the version selected from the Default Clone Protection Version drop-down list available under the Administration Console. |
| Advanced |
Physical Machine Following clone protection schemes are available to protect against the cloning of physical machines:
Virtual Machine Following clone protection schemes are available to protect against the cloning of virtual machines:
|
- See Protection Against Cloning for more information about clone protection.
- For a more detailed description of each of the clone protection schemes see How Sentinel LDK Detects Machine Cloning.
If Sentinel HL locking type is selected, the following check boxes appear:
- Upgrade to Driverless: See Upgrading Sentinel HL keys to Driverless Configuration for details.
- Use Virtual Clock: If you select this option, you will be able to manage time-based licenses for Sentinel HL (Driverless Configuration) keys where no real-time clock is available. A virtual clock will be maintained in such keys.For Products that are licensed with Sentinel SL keys, Sentinel HL Time keys, and Sentinel HL NetTime keys, V-Clock is always available. For details, see Enabling V-Clock for Sentinel HL (Driverless Configuration) Keys.
- Click Add Features. The Add Features to Product pop-up appears.
- Select the Features to add. Click Add Features to Product. The associated Features are displayed in the main screen.
- To remove a Feature from the Product, click Remove in the same row. To remove multiple Features, select the check boxes and click Remove.
- select Can be excluded if you want to enable the order taker to exclude the Feature while generating Entitlements.
- select Always include if you want that the Feature should never be excluded.
You can perform the following actions in this pane:
If you remove a pre-existing Feature, it will still remain as it is in the Product.
If for an existing Feature the license type is Specify at entitlement time, then use Overwrite instead of Modify to change the license terms.
- Save as Draft—To save the Modification Product as Draft so that you can update its details later.
- Save as Complete—This finalizes the Modification Product.
The new Modification Product is displayed in the Products page just below the Base Product.